PROTECTING CUSTOMER DATA IS CRITICAL
Our solution ensures that there are proper safeguards in place that keep consumers personal information safe and secure. Now with even more robust audit tools!
Industry Fact #1
91% OF ALL HACKING STARTS WITH PHISHING
Learn how we help identify, sequester, and mitigate risks of Phishing in your systems.
Privacy & Safeguards Program
LEARN MORE
OUR ROBUST SET OF TOOLS PROTECT VALUABLE DATA
Consumers have a right to know that their data is safe. We have developed a system for keeping it all straight.
Benefits Include:
- ABLE Software Platform
- Vendor Management - Now with AbleAuditor
- Reduces Risk
- Saves Time
TABLE OF CONTENTS
loading...
10-Steps for Navigating FTC Safeguards Compliance
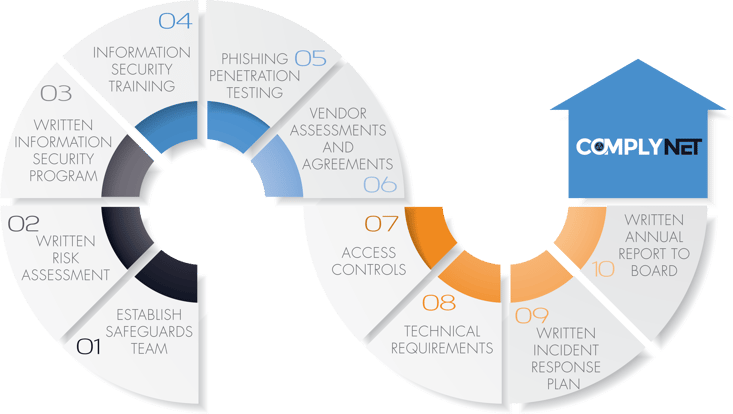
Step 1
Establish Safeguards Team
- Compliance starts with pulling together the right team:
- Designate a "Qualified Individual" to implement, oversee, and enforce the program
- Identify an information technology (IT) resource to oversee technical aspects
- Add a compliance expert to help guide the team
- Establish key performance indicators (KPIs)
- Meet quarterly
- Track progress
Step 2
Written Risk Assessments
- Your dealership must conduct a written risk assessment that will:
- Map customer information (storage, access, and process)
- Identify risks
- Evaluate and categorize risks
- Examine controls and safeguards
- Mitigate identified risks
- Periodically reexamine the controls and safeguards
- Our platform automates the assessment process and documents the controls and safeguards
Step 3
Written Information Security Program
- Your information security program must be comprehensive, based on your written risk assessment, and include:
- Administrative safeguards
- Technical safeguards
- Physical safeguards
- We help custom-tailor a written information security program for your organization
Step 4
Information Security Training
There are security awareness training requirements, and our platform provides your team with necessary trainings, such as:- Privacy and Safeguards
- Privacy and Safeguards for the Shop
- Document and Data Disposal
- Information Security Awareness
- Phishing Awareness
- PCI
Step 5
Phishing Penetration Testing
Over 90% of all hacking starts with phishing, and we will test for your greatest risk by:
- Conducting simulated phishing attacks of company-owned emails
- Providing remedial phishing trainings for team members that:
- Click on links
- Download attachments
- Provide credentials
Step 6
Vendor Assessments and Agreements
- Each service provider with access to customer information must be:
- Capable of appropriately safeguarding customer information
- Assessed to confirm information security practices
- Contractually obligated to appropriately safeguard customer information
- Our platform automates:
- Assessments
- Agreements
- Web Audits using our NEW AbleAuditor, an intelligent discovery audit tool
Step 7
Access Controls
- Access to customer information must be monitored and limited, and change management procedures must be implemented
- Our platform helps evaluate your controls and provides you with important polices and procedures, such as:
- Data and Document Retention Policy
- Data and Document Disposal Policy
- Authorized Use Policy
Step 8
Technical Requirements
Through the assessment process, your information systems will be evaluated to ensure:
- Multi-factor authentication (MFA) is enabled
- Encryption is present
- Continuous monitoring is occurring
- Absent effective continuous monitoring:
- Penetration testing (at least annually)
- Vulnerability scanning (at least every 6 months)
- Absent effective continuous monitoring:
Step 9
Written Incident Response Plan
- Create a written incident response plan that will assist in:
- Responding to a security incident
- Recovering from a security incident
- Remediating the security incident
- Conducting a root cause analysis to help strengthen the information security program
- We help custom-tailor a written information security program for your organizationspan>
Step 10
Written Annual Report to Board (or Equivalent Body)
- The Qualified Individual must create a report (at least annually) identifying overall compliance and material matters, such as:
- Risks assessed, managed, and controlled
- Service provider arrangements
- Testing results
- Security violations, events, and responses
- Proposed changes to the information security program
- We help prepare the annual status report for your Qualified Individual
We're Here To Help
Guided Compliance Consultants
Let us be your trusted advisor to guide you toward a culture of Complete Compliance.
.png?width=288&name=We%20Simplify%20Dealer%20Compliance%20(5).png)
Countdown to Compliance
FTC Deadline has been extended!
You're in luck! There is still time to get your dealership compliant by 6.9.2023.01
Days
23
Hours
45
Minutes
67
Seconds
